Understanding Cloud Assessment: Ensuring Secure and Efficient Cloud Environments
As organizations increasingly adopt cloud computing to enhance operational efficiency, flexibility, and scalability, ensuring the
Read More








Industry-Leading API Vulnerability Scanner


Expert Human Support To Help You Fix Any Issue.







"The VAPT process was seamless and highly detailed. CIBERON's team helped us identify and resolve security gaps effectively, ensuring our network is well-protected against threats."

"CIBERON’s VAPT service gave us an in-depth understanding of our vulnerabilities. The expert recommendations enabled us to proactively address risks and enhance our cybersecurity strategy."

Lorem ipsum dolor sit amet, consectetur adipiscing elit,do eiusmod tempor incididunt ut labore et dolore.

Lorem ipsum dolor sit amet, consectetur adipiscing elit,do eiusmod tempor incididunt ut labore et dolore.

Lorem ipsum dolor sit amet, consectetur adipiscing elit,do eiusmod tempor incididunt ut labore et dolore.

Lorem ipsum dolor sit amet, consectetur adipiscing elit,do eiusmod tempor incididunt ut labore et dolore.







Discover insightful content on our CIBERON blog, where we share expert advice, industry trends, and best practices to strengthen your cybersecurity strategies. Stay informed with actionable insights tailored to help businesses stay secure in a rapidly evolving digital landscape.

As organizations increasingly adopt cloud computing to enhance operational efficiency, flexibility, and scalability, ensuring the
Read More
In an increasingly interconnected world, where organizations rely heavily on digital infrastructure, the security of
Read More
In today’s digital landscape, the threat of cyberattacks looms larger than ever. Organizations are increasingly
Read MoreIn essence, a pen test is more thorough and simulates actual attacks, while a vulnerability scan is a quicker, automated check for known issues.
Penetration tests are typically performed by ethical hackers or security professionals known as penetration testers or pen testers. These individuals have specialized skills and knowledge in cybersecurity and ethical hacking. They may work for:
Pen testers use a variety of tools and techniques to simulate attacks and identify vulnerabilities, helping organizations strengthen their security posture.
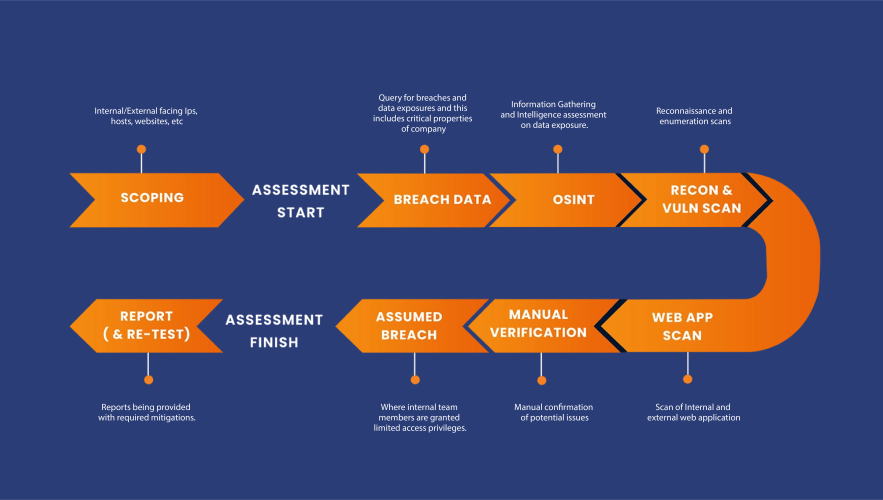
A penetration test typically involves several key steps to thoroughly assess the security of a system. Here are the main phases:
1. Planning and Scoping
2. Reconnaissance
3. Scanning
5. Exploitation
6. Post-Exploitation
7. Reporting
Penetration testing is a critical component of cybersecurity, involving a systematic approach to identify and address vulnerabilities in a system. The process typically begins with planning and reconnaissance to gather information about the target. Then, testers scan the system, identifying and exploiting vulnerabilities using a mix of automated tools and manual techniques. The final steps involve analyzing the results, reporting the findings, and providing recommendations for strengthening the system’s security. This methodical process ensures that security measures are not only in place but also effective against potential cyber threats.
Penetration testing tools are essential for identifying and addressing security vulnerabilities in various systems. Some of the most commonly used tools include Metasploit, known for its exploit development and testing framework, and Astra, which is favored for its diverse infrastructure assessment capabilities. Acunetix is often chosen for automated testing, while Kali Linux is preferred by technical users for its comprehensive suite of testing tools. These tools, among others, provide cybersecurity professionals with the means to conduct thorough and effective security assessments.
The duration of a penetration test can vary widely depending on several factors, including the scope of the test, the size of the environment, and the specific goals set by the organization. Generally, a typical penetration test can take anywhere from one to six weeks. This includes all stages of the process, from planning and execution to analysis, documentation, and the presentation of findings. It’s important to note that these are general estimates, and the actual time may differ based on the complexity of the systems being tested and the depth of the test required.
Penetration testing is a critical security measure that should be performed regularly to protect against evolving cyber threats. The frequency of penetration testing can vary based on several factors, including the nature of your organization, its risk profile, and any applicable regulatory or compliance requirements. Generally, it is recommended to conduct penetration tests at least once a year, but more frequent testing may be necessary for high-profile or high-value organizations. Additionally, retesting should be carried out after any significant changes to your IT environment or when new vulnerabilities are discovered.
Penetration Testing as a Service (PTaaS) is an innovative cybersecurity solution that blends automated tools with human expertise to conduct thorough vulnerability assessments. This service model allows for continuous and dynamic security testing, integrating seamlessly into the software development lifecycle. PTaaS platforms offer a more efficient and flexible approach to identifying and mitigating potential security threats, enabling organizations to rapidly deploy tests and address vulnerabilities with expert guidance.
Utilizing a CREST accredited penetration testing company is crucial because it ensures that the testing is conducted by professionals who adhere to high standards of knowledge, skill, and ethical behavior. CREST, which stands for the Council of Registered Ethical Security Testers, sets the industry benchmark for quality cybersecurity services. Companies with CREST accreditation have proven their expertise through rigorous examinations and are committed to continuous professional development to stay abreast of the latest security threats and testing techniques. This accreditation provides businesses with the confidence that their cybersecurity is thoroughly evaluated, aligning with global best practices and regulatory requirements.
After penetration testing is completed, the ethical hacker compiles a report detailing the vulnerabilities discovered, which the organization can then use to strengthen its security measures. This process often includes a review of the findings, development of a remediation plan, and potentially a retest to validate the effectiveness of the implemented changes. Penetration tests can indeed be performed remotely, utilizing advanced algorithm-based technologies that mimic an ethical hacker’s tools and techniques, allowing for comprehensive security assessments without the need for physical presence.
Choosing a penetration testing supplier is a critical decision that can significantly impact your organization’s security. It’s important to consider certifications, experience, methodologies, and client testimonials when making this choice. Certifications like CEH and CISSP indicate a provider’s expertise, while experience in your industry suggests familiarity with specific security challenges. Methodologies should align with established frameworks like OWASP or NIST, and detailed reports should be provided. If your current supplier meets these criteria and you’ve been satisfied with their service, it may be beneficial to continue the partnership. However, regularly reviewing and comparing options can ensure you’re receiving the best service for your needs.
Penetration testing, commonly referred to as pen testing, is a critical cybersecurity practice that involves simulating cyberattacks to identify vulnerabilities in a system. While it is an essential component of a robust security strategy, it must be carefully managed to minimize disruptions to business operations. Strategies such as conducting tests during off-peak hours, using test copies of live systems, and clear communication with stakeholders can help ensure that business operations continue smoothly during a pen testing exercise.
The cost of penetration testing can vary widely depending on several factors such as the scope of the test, the size of the organization, the complexity of the systems being tested, and the expertise of the testing team. Generally, prices can range from as low as $1,000 to over $100,000. For most organizations, the average cost tends to be between $10,000 and $35,000. It’s important to consider that while upfront costs may seem significant, the investment in a penetration test can be invaluable in protecting against potential security breaches.
Copyright @2024 Ciberon. All Rights Reserved.