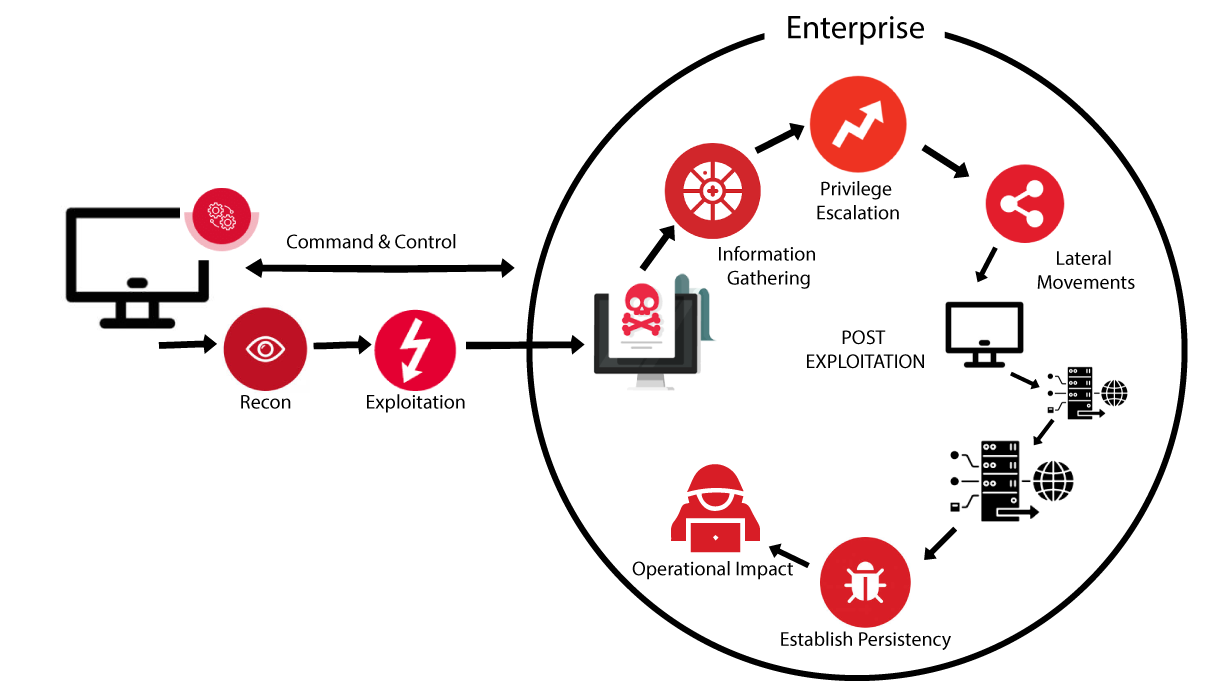
After we compromised one or more devices on the target’s network we make sure we do not lose access to such devices as that would prevent us from completing our final assignment and would require us to start over. Depending on the situation we try to deploy customized malware which allows to reconnect to the infected device whenever we need to continue with our activities. When installation of persistence mechanisms is impossible we attempt to extract certain secrets, such as cached passwords, sensitive documentation, etc. which could help us to continue with the assignment.