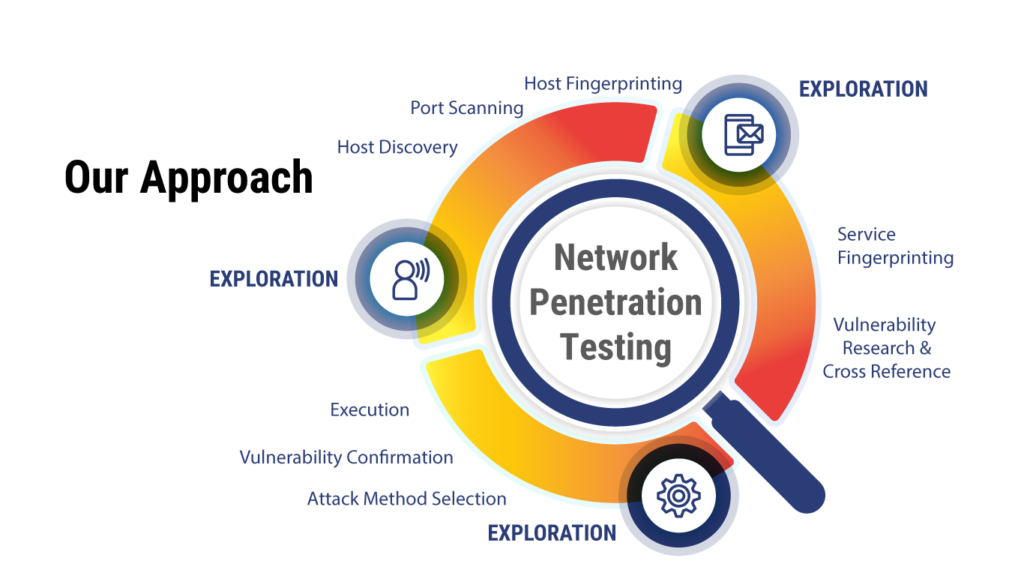
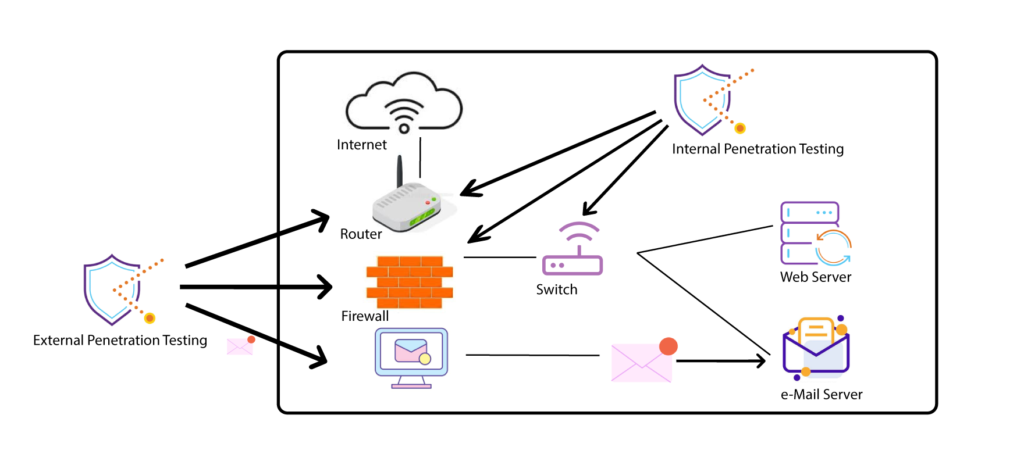
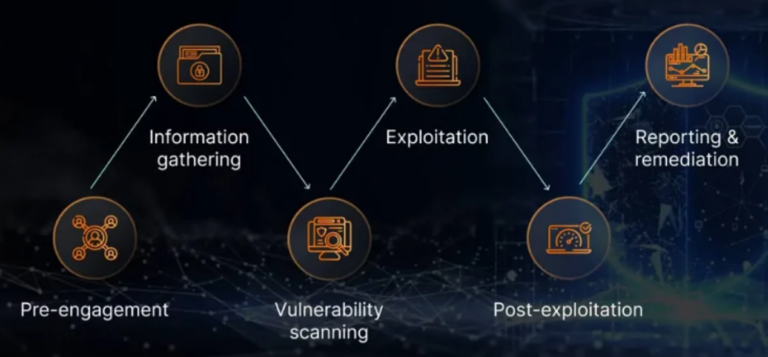
Network penetration testing is one type of penetration testing—or “pen test”—that specifically targets a company’s entire computer network through the practice of ethical hacking. The goal of network penetration testing is to reveal and identify any vulnerabilities within the organization. This includes doing an in-depth evaluation of network security measures through external tests and internal tests, such as web application testing and mock phishing attacks.
Business Benefit of Network Penetration Testing as a Service :
Our network penetration tests have spanned numerous industries, including healthcare, supply chains, IT consulting, product development, and telecommunications in UAE. Additionally, we use the knowledge gained from each pen test to improve the next one.
- Simulating attacks to assess your security posture improves network administration.
- Reduce testing costs without compromising security.
- Deliver audits of network security of the highest quality while reducing compliance costs.
- We reduce complexity by implementing Vulnerability Management and upgrades.
- Reduce the time and effort required to identify and address security flaws
- Training network administrators in remediation reduces security testing expenses.
- Monitoring dashboards for the network's security posture.