Understanding Cloud Assessment: Ensuring Secure and Efficient Cloud Environments
As organizations increasingly adopt cloud computing to enhance operational efficiency, flexibility, and scalability, ensuring the
Read More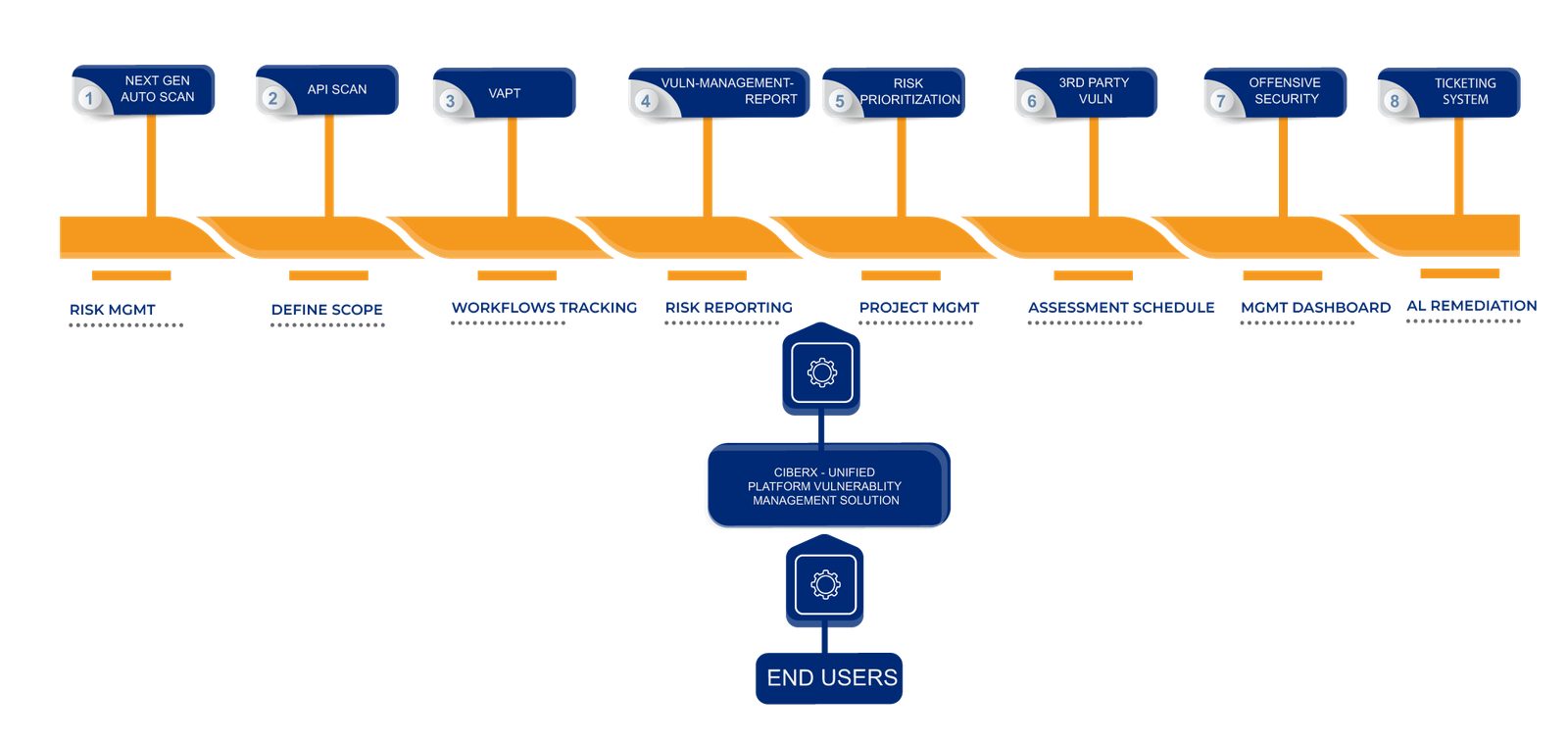









Experience lightning-fast, automated web scanning that detects even the most elusive vulnerabilities, ensuring your web presence is fortified against evolving threats.

Protect your APIs with next-gen scanning technology that offers precise vulnerability detection and seamless integration into your existing security workflows.

Vulnerabilities found through various assessment activities across the IT Infra (Web, Mobile, Servers, Network, etc.) can be easily managed. Assessment independent, vendor independent solution just for your vulnerability management needs.

The process of the solution is based on the Industry Standard for a complete vulnerability management solution. Begin it with Defining the Assessment Activities to be managed, Define the scope of your vulnerability management program & finally add the vulnerabilities.

A seamless workflow-based actions, that lets your teams to be on top of the game & to track the current state of the vulnerably across the assessment activities. An easy to update workflows for the vulnerabilities to track current state.

Total VM can act as your vulnerability reporting portal, for all the assessment activities. Additionally, will allow you to track the entire posture under a single roof. Access all the reports in the same view.

The solution helps create a clear scope for assessment activities by organizing them into distinct projects. Each project is managed independently, allowing for better tracking and management of assessment tasks.

The platform, gives a handy way to schedule your assessment activities, track the progress. It helps you to create an assessment plan.

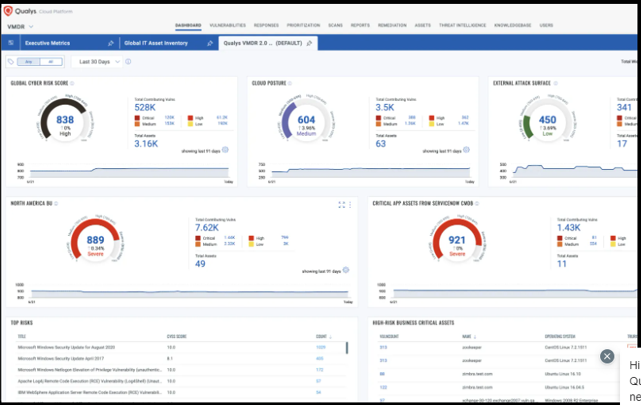
The solution provides a variety of dashboards for teams and management to stay updated on key metrics, such as total vulnerabilities per assessment, aging reports, remediation trends, security posture improvements, and compliance status. It includes dedicated compliance dashboards.

The solution would also suggest the best practices for remediating the vulnerabilities & your team can also get assistance from our experts. Simple patches, upgrades, or code-fixes…!!
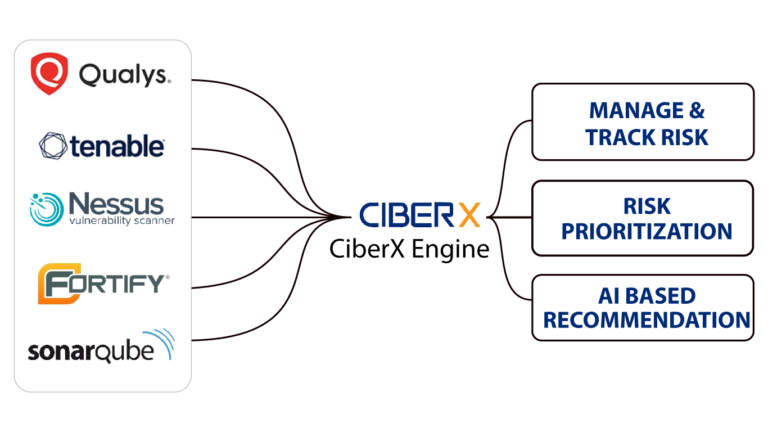







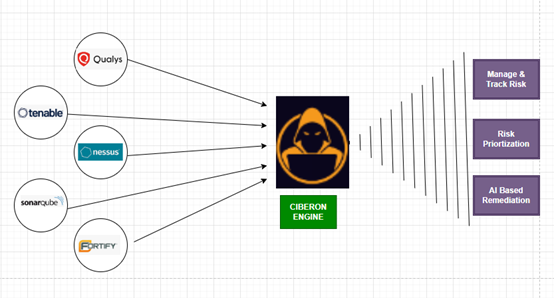
Utilizes AI for accurate risk assessment and remediation
Centralizes various aspects of vulnerability management.
Through ticket integration and workflow-based tracking.
Helps maintain continuous vigilance on vulnerabilities.





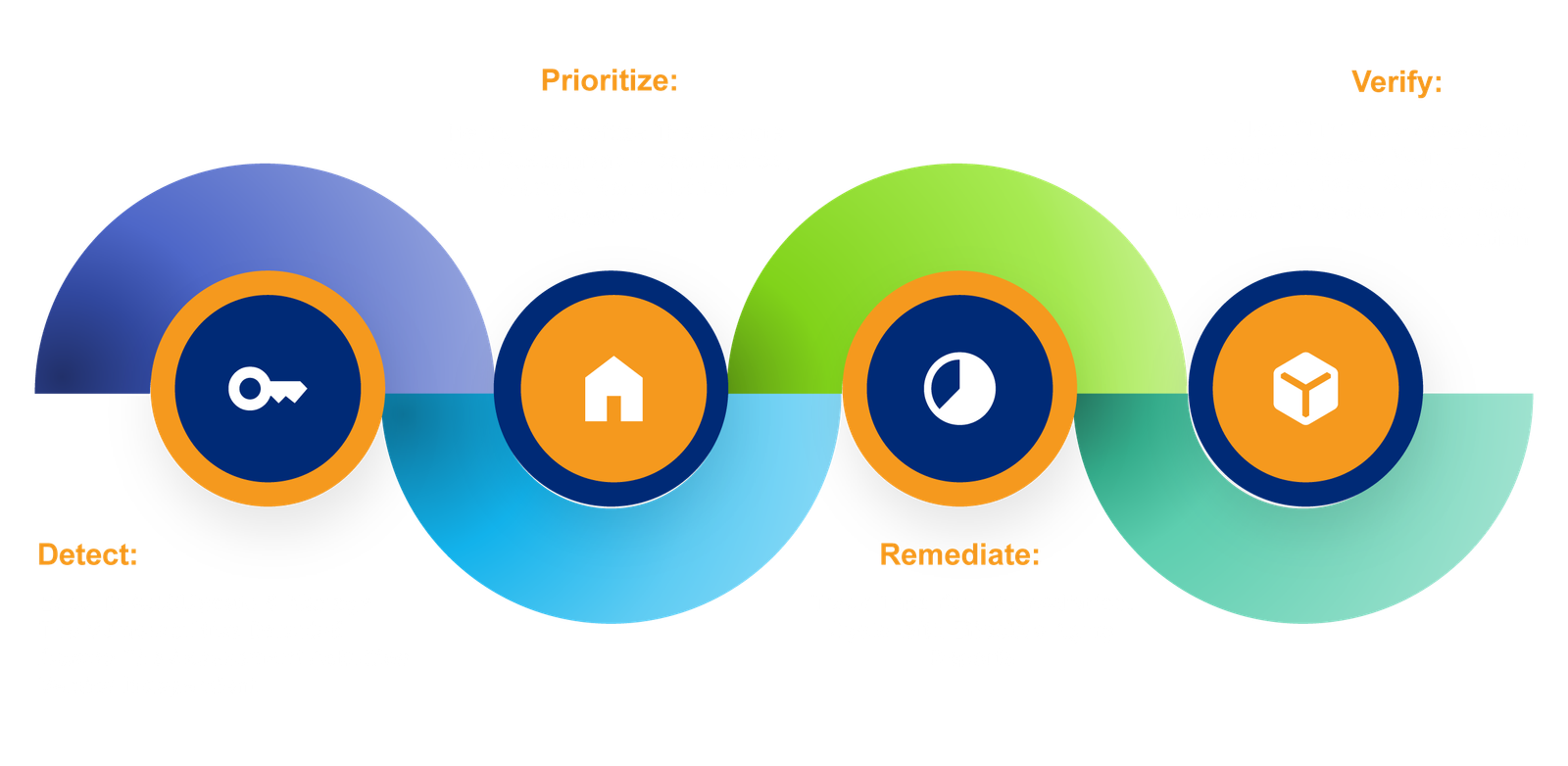
Swiftly uncover, prioritize, and address the most critical cyber threats, compliance breaches, and supply chain vulnerabilities across all your product lines.
Align built-in regulatory policies with comprehensive security assessments, and generate regulator-ready reports for ISO, FDA, UNECE, and over 50 other standards in no time.
Automate every aspect of your workflow to scale operations, from vulnerability management to SBOM validation and product security incident response.





"The VAPT process was seamless and highly detailed. CIBERON's team helped us identify and resolve security gaps effectively, ensuring our network is well-protected against threats."

"CIBERON’s VAPT service gave us an in-depth understanding of our vulnerabilities. The expert recommendations enabled us to proactively address risks and enhance our cybersecurity strategy."

Lorem ipsum dolor sit amet, consectetur adipiscing elit,do eiusmod tempor incididunt ut labore et dolore.

Lorem ipsum dolor sit amet, consectetur adipiscing elit,do eiusmod tempor incididunt ut labore et dolore.

Lorem ipsum dolor sit amet, consectetur adipiscing elit,do eiusmod tempor incididunt ut labore et dolore.

Lorem ipsum dolor sit amet, consectetur adipiscing elit,do eiusmod tempor incididunt ut labore et dolore.







Discover insightful content on our CIBERON blog, where we share expert advice, industry trends, and best practices to strengthen your cybersecurity strategies. Stay informed with actionable insights tailored to help businesses stay secure in a rapidly evolving digital landscape.

As organizations increasingly adopt cloud computing to enhance operational efficiency, flexibility, and scalability, ensuring the
Read More
In an increasingly interconnected world, where organizations rely heavily on digital infrastructure, the security of
Read More
In today’s digital landscape, the threat of cyberattacks looms larger than ever. Organizations are increasingly
Read MoreCIBERX scans your IT environment to identify vulnerabilities, assesses the level of risk associated with each, and provides actionable recommendations for remediation. The platform prioritizes vulnerabilities based on factors like exploitability and impact to streamline security efforts.
CIBERX combines real-time vulnerability intelligence, custom risk scoring, and integration capabilities with third-party tools. It is designed for fast deployment, user-friendly dashboards, and advanced analytics to make vulnerability management more accessible and efficient.
Yes, CIBERX offers continuous vulnerability scanning, which ensures up-to-date security assessments and helps detect new vulnerabilities as they emerge in real time.
CIBERX uses a unique risk scoring system that considers factors such as exploitability, asset criticality, and potential business impact, allowing organizations to focus on the most critical threats.
Yes, CIBERX offers integration with a wide range of security and IT management tools, including SIEMs, ticketing systems, and patch management solutions, enabling seamless workflows and improved incident response.
Yes, CIBERX includes comprehensive compliance reporting for various industry standards like ISO, NIST, GDPR, and DESC, helping organizations maintain regulatory compliance and streamline audits.
CIBERX uses advanced filtering and contextual analysis to minimize false positives. The platform also allows users to manually validate vulnerabilities, ensuring accurate results.
CIBERX adheres to the highest security standards and best practices, including data encryption, secure access controls, and regular security audits, to protect sensitive data and ensure platform integrity.
Yes, all data stored within CIBERX is encrypted at rest and in transit, ensuring your organization’s vulnerability data remains secure.
Yes, CIBERX supports multi-factor authentication to enhance the security of user accounts and prevent unauthorized access.
CIBERX can be deployed in various configurations, including on-premises, in the cloud, or in a hybrid setup, depending on your organization’s requirements and preferences.
CIBERX offers tiered support packages, including 24/7 support for critical issues. Our support team is available to assist with deployment, troubleshooting, and best practices.
Yes, we offer training programs to help your team become proficient with the CIBERX platform, including user guides, webinars, and on-demand resources.
CIBERX pricing is based on factors like the size of the infrastructure being managed and additional features selected. We offer flexible licensing models to meet diverse organizational needs.
Yes, we offer free trials and live demos to help organizations understand the platform’s features and how it can meet their specific requirements.
Deployment begins with an assessment of your infrastructure, followed by the installation of scanning agents or network-based scanning setups. Our support team guides you through configuration and initial scans to ensure optimal performance.
Yes, CIBERX provides a knowledge base with articles, tutorials, and troubleshooting guides, as well as a community forum where users can share insights and solutions.
Yes, CIBERX offers integrated vulnerability assessment tools to aid in VAPT efforts, making it easier for security teams to identify weaknesses and ensure compliance with VAPT requirements.
CIBERX continuously updates its vulnerability database to include the latest threat intelligence, ensuring that users stay informed about emerging threats and potential exploits.
Yes, CIBERX adheres to DESC certification standards, ensuring compliance with regional VAPT requirements, especially in regions like the UAE where DESC certification is mandatory.
Copyright @2024 Ciberon. All Rights Reserved.